TPMLookup, a crucial component of modern security systems, allows access to vital data stored within the Trusted Platform Module (TPM). This guide delves into the functionality, security implications, and practical applications of TPM lookups across various operating systems and hardware configurations. We will explore both basic and advanced techniques, providing a comprehensive understanding of this essential security tool.
Understanding TPM lookups is vital for anyone involved in system security, from administrators securing their infrastructure to developers integrating TPM functionality into their applications. This guide aims to bridge the gap between theoretical knowledge and practical application, empowering readers to confidently utilize and secure TPM lookups within their respective environments.
TPM Lookup Functionality
A TPM (Trusted Platform Module) lookup operation allows access to various data stored securely within the TPM chip. This functionality is crucial for various security applications, enabling verification of system integrity and authentication processes. Understanding the mechanics and security implications of TPM lookups is paramount for system administrators and security professionals.
TPMlookup, a tool for accessing specific system information, can sometimes indirectly relate to public records. For instance, investigating an individual might lead you to resources like the Tygart Valley Regional mugshots, which you can find here: tygart valley regional mugshots. Returning to TPMlookup, remember that its primary function is focused on internal system details, not public records searches.
TPM Data Retrieval
TPM lookups can retrieve several types of data, depending on the specific operation and the data previously stored within the TPM. This includes, but is not limited to, platform configuration registers (PCR) values, endorsement keys (EK), and stored secrets. Access to this data is typically controlled through hierarchical key structures and authorization mechanisms, ensuring only authorized entities can retrieve specific information.
TPM Lookup Use Cases
TPM lookups are employed across a range of security scenarios. Common use cases include:
- System Integrity Verification: Checking the PCR values to ensure the system hasn’t been tampered with since the last boot.
- Secure Boot Verification: Confirming that the boot process followed a trusted chain of execution.
- Disk Encryption Key Management: Retrieving encryption keys for disk drives, ensuring only authorized users can access data.
- Remote Attestation: Proving the integrity and authenticity of a remote system to a trusted authority.
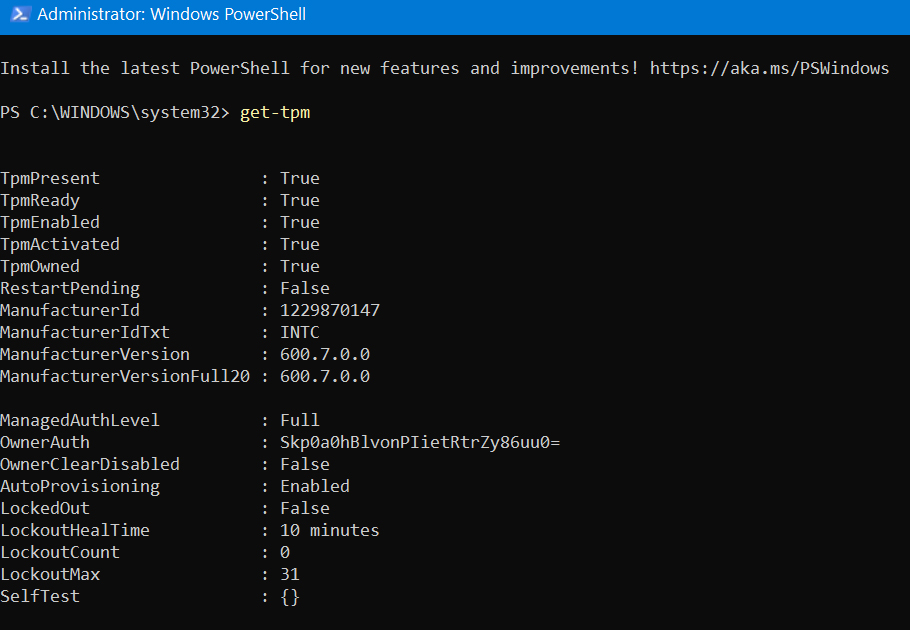
Performing a TPM Lookup via CLI
Source: monitorteknologi.com
The exact commands vary depending on the operating system and TPM implementation. However, a general procedure can be Artikeld:
| Step | Command | Description | Expected Output |
|---|---|---|---|
| 1 | tpm2_getrandom |
Generates random numbers using the TPM’s internal random number generator. This is often a prerequisite for other operations. | A sequence of random bytes. |
| 2 | tpm2_pcrread |
Reads the value of a specific Platform Configuration Register (PCR). Replace |
The current value of the specified PCR. |
| 3 | tpm2_nvread |
Reads data from a Non-Volatile Storage (NVS) area within the TPM. Replace |
The data stored in the specified NVS area. |
| 4 | tpm2_getcap |
Retrieves information about TPM capabilities. Replace |
Information about the specified TPM capability. |
TPM Lookup Security Implications
Improper implementation of TPM lookups can introduce significant security risks. Secure key management and robust error handling are crucial for mitigating these risks.
Secure Key Management and Vulnerabilities
Source: prajwaldesai.com
Secure key management is paramount. Compromised keys can allow unauthorized access to sensitive data retrieved during TPM lookups. Potential vulnerabilities include:
- Weak Key Generation: Using inadequate algorithms or insufficient entropy for key generation.
- Improper Key Storage: Storing keys insecurely, making them vulnerable to theft or unauthorized access.
- Insufficient Key Rotation: Failing to regularly update keys, increasing the risk of compromise.
- Side-Channel Attacks: Exploiting timing or power consumption variations during TPM operations to extract sensitive information.
Secure Architecture for TPM Lookups
A secure architecture for TPM lookups should incorporate:
- Strong Cryptography: Using robust cryptographic algorithms and key lengths.
- Hardware Security Modules (HSMs): Protecting keys within tamper-resistant hardware.
- Secure Boot: Ensuring the system boots from trusted components.
- Access Control: Implementing strict access control mechanisms to limit access to TPM operations.
- Regular Security Audits: Performing regular audits to identify and address potential vulnerabilities.
TPM Lookup and Different Operating Systems
TPM lookup methods differ across operating systems. While the underlying TPM functionality remains consistent, the interfaces and tools used to interact with the TPM vary significantly.
OS-Specific TPM Lookup Methods
| OS | Methods | Description |
|---|---|---|
| Windows | tpm.msc (GUI), PowerShell cmdlets, Windows API | Provides a range of tools and APIs for interacting with the TPM, including GUI management tools and programmatic access. |
| Linux | tpm2-tools (CLI), various libraries (e.g., TSS) | Relies on command-line tools and libraries for interacting with the TPM. The specific tools and libraries may vary depending on the distribution. |
| macOS | tpm2-tools (CLI), limited system-level APIs | Similar to Linux, primarily uses command-line tools. Direct system-level access to TPM functions is more limited compared to Windows. |
Error Handling and Output Formats
Error handling and output formats differ across operating systems. Windows typically provides more user-friendly error messages, while Linux and macOS may provide more technical, low-level error codes. Understanding these differences is crucial for effective troubleshooting.
TPM Lookup and Hardware Variations: Tpmlookup
Different TPM hardware versions (e.g., TPM 1.2, TPM 2.0) have varying capabilities and functionalities. Understanding these differences is essential for ensuring compatibility and correct interpretation of lookup results.
TPM Version Compatibility and Limitations
TPM 2.0 offers significant improvements over TPM 1.2, including enhanced security features and a more robust command set. However, older systems may only support TPM 1.2, limiting the available lookup operations and data that can be retrieved. Applications designed for TPM 2.0 may not be compatible with TPM 1.2, and vice versa. Careful consideration of TPM version compatibility is crucial during development and deployment.
Impact of TPM Hardware Specifications
The specific hardware specifications of a TPM influence the data available during a lookup. For instance, the size of the Non-Volatile Storage (NVS) area varies across TPM versions and manufacturers. The available PCR banks and their sizes also differ, affecting the amount of platform configuration data that can be stored and retrieved.
Handling Different TPM Hardware Versions
Robust TPM lookup implementations should incorporate mechanisms for detecting and handling different TPM hardware versions. This may involve using conditional logic based on TPM version detection or employing abstraction layers to hide the underlying hardware differences from the application logic. This ensures consistent functionality across different TPM hardware.
Troubleshooting TPM Lookup Issues
TPM lookups can fail due to various reasons. A systematic approach to troubleshooting is essential for identifying and resolving these issues.
Common TPM Lookup Errors and Solutions
- TPM not found: Verify that the TPM is properly installed and enabled in the BIOS/UEFI settings.
- Incorrect permissions: Ensure the user or process has the necessary permissions to access the TPM.
- Invalid command parameters: Double-check the command syntax and parameters used in the TPM lookup operation.
- TPM communication errors: Verify that the communication channels between the system and the TPM are functioning correctly.
- TPM hardware failure: In case of persistent errors, consider replacing the TPM module.
- Driver issues: Ensure that the necessary TPM drivers are installed and updated.
- Incorrect key usage: Verify that the correct keys are being used for the operation and that they have not expired.
Advanced TPM Lookup Techniques
Advanced techniques can optimize TPM lookup performance and enhance security. These include leveraging TPM-based attestation and integrating TPM lookups with other security mechanisms.
Optimizing TPM Lookup Performance, Tpmlookup
Optimizing TPM lookup performance often involves minimizing the number of TPM calls and efficiently managing data transfer between the system and the TPM. Caching frequently accessed data and using asynchronous operations can significantly improve performance.
TPM-Based Attestation
TPM-based attestation uses the TPM to cryptographically prove the integrity and authenticity of a system. This enhances the security of TPM lookups by ensuring that the data retrieved comes from a trusted source.
Integration with Other Security Mechanisms
Integrating TPM lookups with other security mechanisms, such as cryptographic libraries and secure enclaves, can further enhance security. This allows for secure key management, data protection, and authentication processes.
Secure Remote TPM Lookup
Implementing a secure remote TPM lookup requires careful consideration of network security and authentication. Using secure communication protocols (e.g., TLS) and robust authentication mechanisms is essential to prevent unauthorized access and data tampering during remote TPM operations.
Ultimate Conclusion
Mastering TPM lookups requires a thorough understanding of their functionality, security implications, and operational nuances across diverse systems. This guide has provided a comprehensive overview, from basic operations to advanced techniques, equipping you with the knowledge to effectively utilize and secure TPM lookups. Remember that robust security practices, including secure key management, are paramount to mitigating potential risks. By understanding and implementing these best practices, you can significantly enhance the overall security posture of your systems.
