ATK Model Blog A Comprehensive Guide
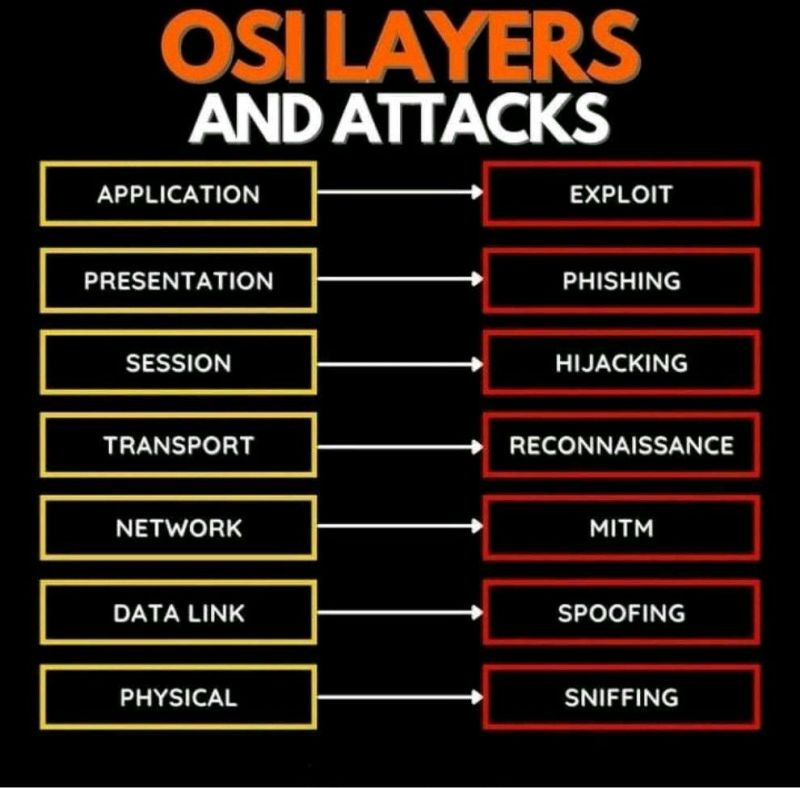
ATK Model Blog sets the stage for this exploration, offering a detailed examination of Attacker Knowledge (ATK) models as discussed in various blog posts. We’ll delve into different ATK model types, successful implementations, key features, and benefits, providing a comprehensive overview for both newcomers and experienced practitioners. This analysis will cover technical aspects, including code … Read more