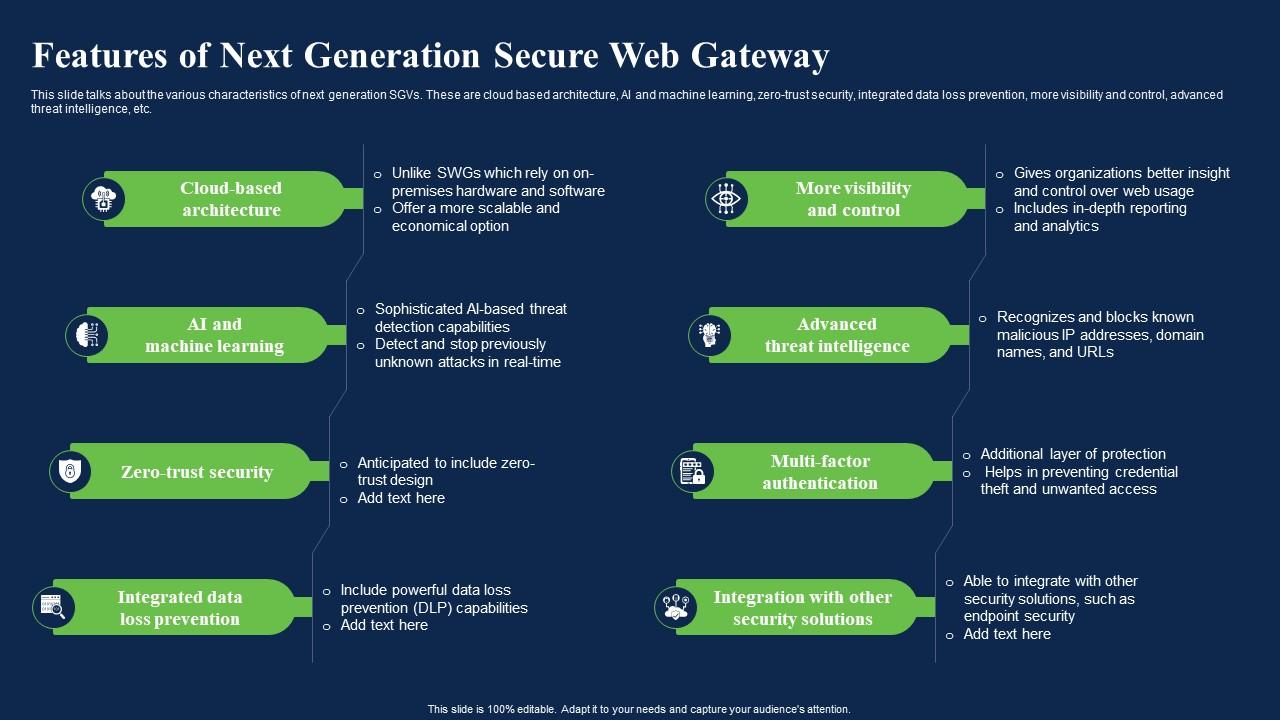
NextGen Securus Advanced Security Solutions
NextGen Securus represents a significant leap forward in cybersecurity, offering robust protection against evolving threats. This comprehensive system leverages cutting-edge technologies to safeguard sensitive data and critical infrastructure, providing a superior level of security compared to previous generations. We will explore its core functionalities, implementation, and the significant return on investment it offers organizations of … Read more